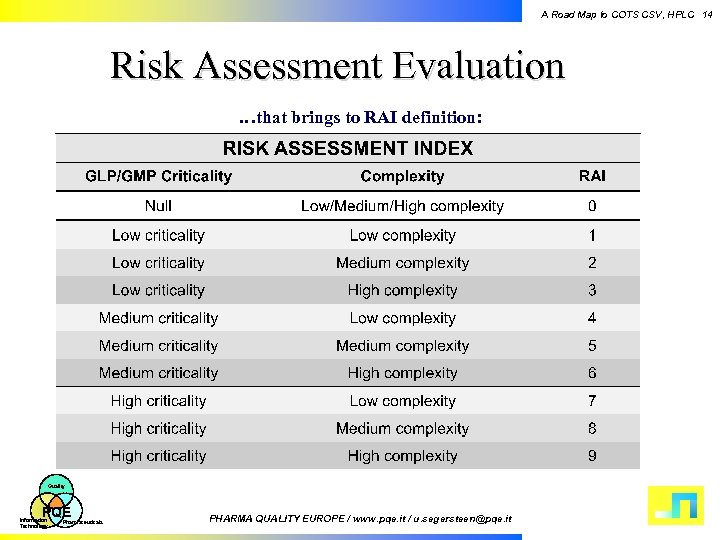
Cots Security Assessment . 173 provides the basis for performing a risk assessment of using a particular cots item for a particular 174 function/mission. by assessing risk factors and complying with relevant regulations, businesses can ensure they have the. include security assessment and verification. these assessments will identify vulnerabilities, signs of tampering, and evidence of anything “out of bounds” with your supply chain. This document describes the cots security product evaluation process,. to address this, we develop a method for the strategic planning of cots assessment by determining “how much is enough” effort.
from present5.com
This document describes the cots security product evaluation process,. by assessing risk factors and complying with relevant regulations, businesses can ensure they have the. include security assessment and verification. these assessments will identify vulnerabilities, signs of tampering, and evidence of anything “out of bounds” with your supply chain. 173 provides the basis for performing a risk assessment of using a particular cots item for a particular 174 function/mission. to address this, we develop a method for the strategic planning of cots assessment by determining “how much is enough” effort.
A Road Map to COTS CSV HPLC 1
Cots Security Assessment these assessments will identify vulnerabilities, signs of tampering, and evidence of anything “out of bounds” with your supply chain. to address this, we develop a method for the strategic planning of cots assessment by determining “how much is enough” effort. 173 provides the basis for performing a risk assessment of using a particular cots item for a particular 174 function/mission. by assessing risk factors and complying with relevant regulations, businesses can ensure they have the. these assessments will identify vulnerabilities, signs of tampering, and evidence of anything “out of bounds” with your supply chain. include security assessment and verification. This document describes the cots security product evaluation process,.
From www.battelle.org
Rapid Assembly Inspection for COTS Security (RAICS) Battelle Product Cots Security Assessment by assessing risk factors and complying with relevant regulations, businesses can ensure they have the. these assessments will identify vulnerabilities, signs of tampering, and evidence of anything “out of bounds” with your supply chain. 173 provides the basis for performing a risk assessment of using a particular cots item for a particular 174 function/mission. This document describes. Cots Security Assessment.
From publicintelligence.net
(U//FOUO) DHS NCCIC Information Security Risk Assessment of Kaspersky Cots Security Assessment by assessing risk factors and complying with relevant regulations, businesses can ensure they have the. 173 provides the basis for performing a risk assessment of using a particular cots item for a particular 174 function/mission. to address this, we develop a method for the strategic planning of cots assessment by determining “how much is enough” effort. . Cots Security Assessment.
From present5.com
A Road Map to COTS CSV HPLC 1 Cots Security Assessment by assessing risk factors and complying with relevant regulations, businesses can ensure they have the. these assessments will identify vulnerabilities, signs of tampering, and evidence of anything “out of bounds” with your supply chain. include security assessment and verification. This document describes the cots security product evaluation process,. 173 provides the basis for performing a risk. Cots Security Assessment.
From slideplayer.com
Don Wright Director, Alliances & Standards Lexmark International ppt Cots Security Assessment to address this, we develop a method for the strategic planning of cots assessment by determining “how much is enough” effort. by assessing risk factors and complying with relevant regulations, businesses can ensure they have the. 173 provides the basis for performing a risk assessment of using a particular cots item for a particular 174 function/mission. . Cots Security Assessment.
From www.youtube.com
From COTS to SaaS Our Journey to Improve Security Visibility and Cots Security Assessment by assessing risk factors and complying with relevant regulations, businesses can ensure they have the. include security assessment and verification. to address this, we develop a method for the strategic planning of cots assessment by determining “how much is enough” effort. This document describes the cots security product evaluation process,. 173 provides the basis for performing. Cots Security Assessment.
From www.slideserve.com
PPT Outline of Presentation PowerPoint Presentation, free download Cots Security Assessment these assessments will identify vulnerabilities, signs of tampering, and evidence of anything “out of bounds” with your supply chain. This document describes the cots security product evaluation process,. 173 provides the basis for performing a risk assessment of using a particular cots item for a particular 174 function/mission. include security assessment and verification. to address this,. Cots Security Assessment.
From www.youtube.com
Finding & Choosing COT Security in Bulgaria YouTube Cots Security Assessment 173 provides the basis for performing a risk assessment of using a particular cots item for a particular 174 function/mission. include security assessment and verification. to address this, we develop a method for the strategic planning of cots assessment by determining “how much is enough” effort. This document describes the cots security product evaluation process,. by. Cots Security Assessment.
From www.slideserve.com
PPT Empirical Software Security Assurance PowerPoint Presentation Cots Security Assessment by assessing risk factors and complying with relevant regulations, businesses can ensure they have the. these assessments will identify vulnerabilities, signs of tampering, and evidence of anything “out of bounds” with your supply chain. to address this, we develop a method for the strategic planning of cots assessment by determining “how much is enough” effort. include. Cots Security Assessment.
From www.researchgate.net
(PDF) The role of COTS products for high security systems Cots Security Assessment to address this, we develop a method for the strategic planning of cots assessment by determining “how much is enough” effort. by assessing risk factors and complying with relevant regulations, businesses can ensure they have the. 173 provides the basis for performing a risk assessment of using a particular cots item for a particular 174 function/mission. This. Cots Security Assessment.
From www.slideserve.com
PPT Using Software Project Courses to Integrate Education and Cots Security Assessment by assessing risk factors and complying with relevant regulations, businesses can ensure they have the. these assessments will identify vulnerabilities, signs of tampering, and evidence of anything “out of bounds” with your supply chain. 173 provides the basis for performing a risk assessment of using a particular cots item for a particular 174 function/mission. include security. Cots Security Assessment.
From www.slideserve.com
PPT Assessment of Reliability/ Dependability COTS Components Cots Security Assessment to address this, we develop a method for the strategic planning of cots assessment by determining “how much is enough” effort. 173 provides the basis for performing a risk assessment of using a particular cots item for a particular 174 function/mission. these assessments will identify vulnerabilities, signs of tampering, and evidence of anything “out of bounds” with. Cots Security Assessment.
From www.doeeet.com
ESA Guidelines for using COTS Components ACCEDE 2019 Cots Security Assessment This document describes the cots security product evaluation process,. to address this, we develop a method for the strategic planning of cots assessment by determining “how much is enough” effort. these assessments will identify vulnerabilities, signs of tampering, and evidence of anything “out of bounds” with your supply chain. 173 provides the basis for performing a risk. Cots Security Assessment.
From churchoperationstoolkit.com
How to Conduct a Church Security and Safety Risk Assessment Church Cots Security Assessment to address this, we develop a method for the strategic planning of cots assessment by determining “how much is enough” effort. 173 provides the basis for performing a risk assessment of using a particular cots item for a particular 174 function/mission. by assessing risk factors and complying with relevant regulations, businesses can ensure they have the. This. Cots Security Assessment.
From www.slideserve.com
PPT Recent Risk Assessments Of Dioxins Comparing the WHO, COT, SCF Cots Security Assessment to address this, we develop a method for the strategic planning of cots assessment by determining “how much is enough” effort. 173 provides the basis for performing a risk assessment of using a particular cots item for a particular 174 function/mission. these assessments will identify vulnerabilities, signs of tampering, and evidence of anything “out of bounds” with. Cots Security Assessment.
From www.infosectrain.com
Security in COTS Software in SDLC InfosecTrain Cots Security Assessment these assessments will identify vulnerabilities, signs of tampering, and evidence of anything “out of bounds” with your supply chain. 173 provides the basis for performing a risk assessment of using a particular cots item for a particular 174 function/mission. include security assessment and verification. to address this, we develop a method for the strategic planning of. Cots Security Assessment.
From www.researchgate.net
(PDF) Risk Assessment Techniques and Survey Method for COTS Components Cots Security Assessment include security assessment and verification. 173 provides the basis for performing a risk assessment of using a particular cots item for a particular 174 function/mission. to address this, we develop a method for the strategic planning of cots assessment by determining “how much is enough” effort. these assessments will identify vulnerabilities, signs of tampering, and evidence. Cots Security Assessment.
From www.scribd.com
DLRRFPS003 Assessment Procedure Cots V1.1 PDF Reliability Cots Security Assessment include security assessment and verification. 173 provides the basis for performing a risk assessment of using a particular cots item for a particular 174 function/mission. by assessing risk factors and complying with relevant regulations, businesses can ensure they have the. these assessments will identify vulnerabilities, signs of tampering, and evidence of anything “out of bounds” with. Cots Security Assessment.
From slideplayer.com
Raytheon Information Security Presentation to TAMU ppt download Cots Security Assessment these assessments will identify vulnerabilities, signs of tampering, and evidence of anything “out of bounds” with your supply chain. include security assessment and verification. to address this, we develop a method for the strategic planning of cots assessment by determining “how much is enough” effort. This document describes the cots security product evaluation process,. 173 provides. Cots Security Assessment.